|
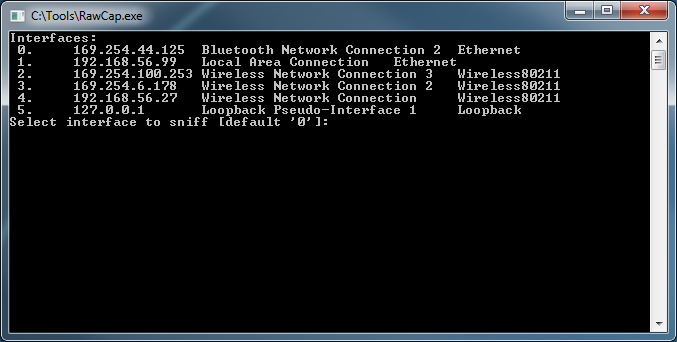
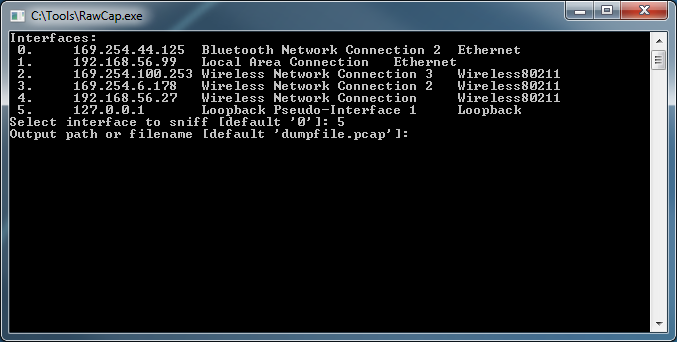
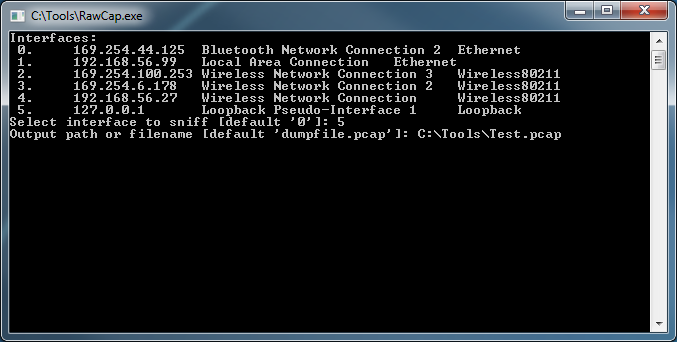
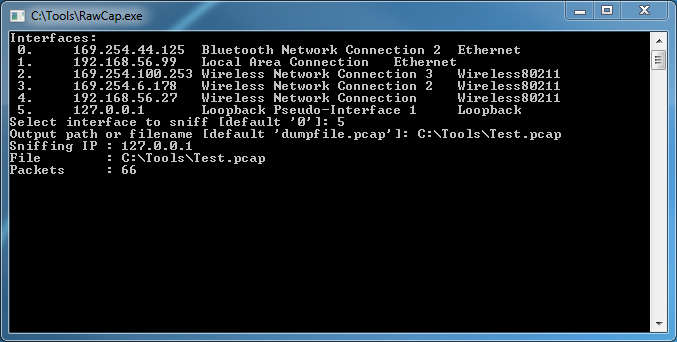
I was recently writing a TCP connector for MySQL so that I could call it from both 64-bit LabVIEW and LabVIEW RT and I realized that I needed a way to spy on my localhost network traffic for debug purposes. So I fired up WireShark, but it turns out that WireShark can't see localhost traffic because localhost traffic is not sent over a real network interface. You can't capture on the local loopback address 127.0.0.1 with WinPcap because... You can, however, use a raw socket sniffer like RawCap to capture localhost network traffic in Windows. When you launch RawCap you will see this simple interface: If you want to monitor your loopback address simply hit "5" on your keyboard to select the loopback pseudo-interface. Give it a file to save the capture to, and be sure to give the file a *.pcap extension so that you can open it with WireShark. As soon as you hit enter RawCap will start capturing traffic on the loopback interface. You should be able to watch the "Packets" count grow. Once RawCap is running go ahead and fire up the process you want to monitor. Once you are done capturing data, hit "Ctrl+C" to stop your capture and close RawCap. You can now open your Test.pcap file with wireshark, and you will see that every 5 seconds National Instruments is doing something over localhost... Hope this is helpful! Jon McBee is a Principal Software Engineer at Cambridge NanoTech and is a Certified LabVIEW Architect, Certified LabVIEW Embedded Developer, Certified TestStand Developer, an NI Certified Professional Instructor, and a LabVIEW Champion
4 Comments
Thoric
8/24/2015 01:11:26 am
Very useful, thanks Jon!
Reply
Jim Fowler
11/17/2015 11:50:47 am
This tool has so many uses - debugging HTTP headers when a server is picky, documenting and mimicking the protocol of a proprietary device (hypothetically speaking, of course), or maybe discovering which ports something is really using, regardless of its documentation.
Reply
Please try Npcap: https://github.com/nmap/npcap, it is based on WinPcap and supports loopback traffic capturing on Windows. Npcap is a subproject of Nmap (http://nmap.org/), so please report any issues on Nmap's development list (http://seclists.org/nmap-dev/).
Reply
Nikolai Safronov
5/25/2016 09:22:47 am
Thanks! Great post!
Reply
Leave a Reply. |
Tags
All
Archives
October 2019
LabVIEW Blogs |
 RSS Feed
RSS Feed
